THE COORDINATE RATIOS AS A TOOL TO ANALYZE THE INTRUSION BASED ON BUŽEK-HILLERY QUANTUM COPYING MACHINE
Besma Othmani1, Mohsen Machhout1, Houcine Mejri1,2, Hafedh Belmabrouk1, Rached Tourki1
1Laboratoire d’Electronique et Micro Electronique Faculté des Sciences de Monastir, 5000 Monastir, Tunisia
2Unité de Mathématiques Appliquées et Physique Mathématique, Ecole Préparatoire aux Académies Mélitaires Avenue Maréchal Tito 4029 Sousse, Tunisia
ABSTRACT
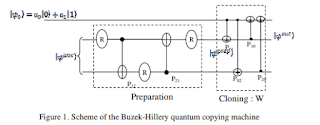
The intrusion based on Bužek-Hillery universal quantum copying machine (UQCM) is investigated. A major problem to the eavesdropper Eve is how to choose the intrusion parameters required by the copying machine in order to take out the maximum of information on the transmitted qubits while making her intrusion as discrete as possible. The present paper attempts to investigate the equatorial and isotropic cloning by means of coordinate ratios. The degree of intrusion is evaluated by means of the ratios of the receiver (Bob) coordinates and the eavesdropper (Eve) coordinates to the sender (Alice) coordinates in the Bloch sphere. The fidelity has been usually used as a criterion to analyze the intrusion. More especially, this fidelity can achieve the value 0.85 for equatorial qubits by using Bužek-Hillery 1→2 machine. Our goal is to study the behavior of these ratios as a function of the intrusion parameters. As has been found, the coordinate ratios of both the receiver and the eavesdropper achieve an optimal value higher than 2/3, in contrast to the isotropic cloning. This can favor the eavesdropping when using equatorial qubits. For isotropic cloning, the maximal intrusion is reached when the coordinate ratios are equal. The optimal values of the intrusion parameters are then evaluated.
KEYWORDS
Eavesdropping, intrusion, quantum copying machines, isotropic cloning, equatorial cloning, coordinate ratios, fidelity
Original Source Link : http://airccse.org/journal/nsa/0112nsa12.pdf





No comments:
Post a Comment