AN EFFECTIVE PREVENTION OF ATTACKS USING GI TIME FREQUENCY ALGORITHM UNDER DDOS
K.Kuppusamy1 and S.Malathi2
1Department of Computer Science &Engineering, Alagappa University, Karaikudi
2Research Scholar, Manonmaniam Sundaranar University, Tirunelvelli
ABSTRACT
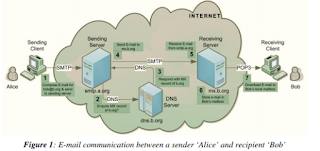
With the tremendous growth of internet services, websites are becoming indispensable. When the number of users gets increased accessing the websites, the performance of the server gets down. Due to much burden on the server, the response time gets delayed. When the process becomes slow, the ratio of the users accessing to the site also goes down. Apart from this, it may also happen due to the attack of Hackers. We have implemented a special kind of technique to recognize the attack carried out by the hackers and block them from using the site. This is termed as Denial of Service and thus is carried out among the web users and is commonly referred to as Distributed Denial of Service (DDoS). To improve server performance and deny the accessibility permissions to the hackers are proposed in this paper.
KEYWORDS
Websites, Attack, Hacker, DDoS
Original Source Link : http://airccse.org/journal/nsa/1111nsa19.pdf