TECHNIQUES AND TOOLS FOR FORENSIC INVESTIGATION OF E-MAIL
M. Tariq Banday
P. G. Department of Electronics and Instrumentation Technology University of Kashmir, Srinagar - 6, India
ABSTRACT
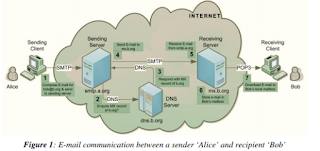
E-mail has emerged as the most important application on Internet for communication of messages, delivery of documents and carrying out of transactions and is used not only from computers but many other electronic gadgets like mobile phones. Over a period of year’s e-mail protocols have been secured through several security extensions and producers, however, cybercriminals continue to misuse it for illegitimate purposes by sending spam, phishing e-mails, distributing child pornography, and hate emails besides propagating viruses, worms, hoaxes and Trojan horses. Further, Internet infrastructure misuse through denial of service, waste of storage space and computational resources are costing every Internet user directly or indirectly. It is thus essential to identify and eliminate users and machines misusing e-mail service. E-mail forensic analysis is used to study the source and content of e-mail message as evidence, identifying the actual sender, recipient and date and time it was sent, etc. to collect credible evidence to bring criminals to justice. This paper is an attempt to illustrate e-mail architecture from forensics perspective. It describes roles and responsibilities of different e-mail actors and components, itemizes meta-data contained in e-mail headers, and lists protocols and ports used in it. It further describes various tools and techniques currently employed to carry out forensic investigation of an e-mail message.
KEYWORDS
E-mail Forensics; E-mail Headers; E-mail Security; Header Analysis; E-mail Architecture
Original Source Link : http://airccse.org/journal/nsa/1111nsa17.pdf





No comments:
Post a Comment