International Journal of Network Security & Its Applications (IJNSA) - ERA, WJCI Indexed
ISSN: 0974 - 9330 (Online); 0975 - 2307 (Print)
Webpage URL: https://airccse.org/journal/ijnsa.html
Using a Deep Understanding of Network Activities for Security Event Management
Mona Lange1, Felix Kuhr2 and Ralf Moller1, 1Universitat zu Lubeck, Germany and 2Technical Universitat Hamburg-Harburg, Germany
Abstract
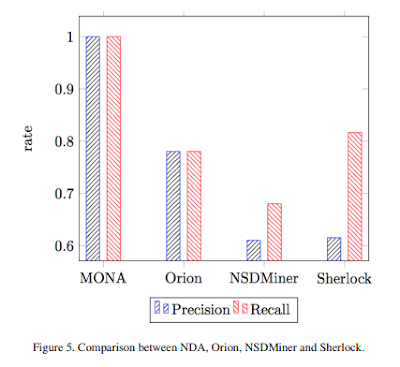
With the growing deployment of host-based and network-based intrusion detection systems in increasingly large and complex communication networks, managing low-level alerts from these systems becomes critically important. Probes of multiple distributed firewalls (FWs), intrusion detection systems (IDSs) or intrusion prevention systems (IPSs) are collected throughout a monitored network such that large series of alerts (alert streams) need to be fused. An alert indicates an abnormal behavior, which could potentially be a sign for an ongoing cyber attack. Unfortunately, in a real data communication network, administrators cannot manage the large number of alerts occurring per second, in particular since most alerts are false positives. Hence, an emerging track of security research has focused on alert correlation to better identify true positive and false positive. To achieve this goal we introduce Mission Oriented Network Analysis (MONA). This method builds on data correlation to derive network dependencies and manage security events by linking incoming alerts to network dependencies.
Keywords
Network Dependency Analysis, Security Event Management, Data Correlation
Original Source URL: https://aircconline.com/ijnsa/V8N3/8316ijnsa01.pdf
Volume URL: https://airccse.org/journal/jnsa16_current.html




No comments:
Post a Comment